ISO/IEC 27001:2022 Certification - The Cybersecurity Priority For 2026

Introduction
By 2026, information security will sit at the centre of almost every business decision. Cloud platforms shared data lakes remote work and complex supplier networks mean that one weak control can affect customers regulators partners and reputation at the same time. Cyber incidents are no longer only an IT problem. They disrupt operations delay orders damage payment flows and expose personal or confidential data.
ISO/IEC 27001:2022 gives organizations a clear method to manage information security risks. It connects policies roles risk assessment technical and physical controls supplier oversight and incident response into one system. When used well it fits how people actually work across office sites home networks factories and cloud tools.
If your organization wants to turn information security into a structured management system for 2026, you can request an ISO/IEC 27001 audit plan from Pacific Certifications to discuss scope timelines and evidence requirements.
Quick summary
ISO/IEC 27001:2022 is the leading standard for information security management systems. It helps organizations define scope assign responsibilities assess risks choose and maintain controls monitor performance handle incidents and keep leadership involved. In 2026 it will be one of the most important certifications for businesses that handle sensitive data work with global clients or rely on digital services and outsourced IT.
Why ISO/IEC 27001:2022 matters?
Most organizations now run critical processes on shared infrastructure and external services. Customer data HR records design pricing logic source code and operational dashboards often sit across several cloud platforms. At the same time many teams work in hybrid patterns and suppliers may handle hosting development support and analytics.
Without a structured system it is easy for access rights to drift policies to stay unread and new projects to launch without risk review. ISO/IEC 27001:2022 matters because it turns information security into a repeatable cycle.
What are the requirements for ISO/IEC 27001:2022?
Most organizations treat the 2022 version of ISO/IEC 27001 as a structured checklist for information security management. It mixes system requirements with an updated control set so that both governance and technical issues are covered. Below are some of the key requirements:
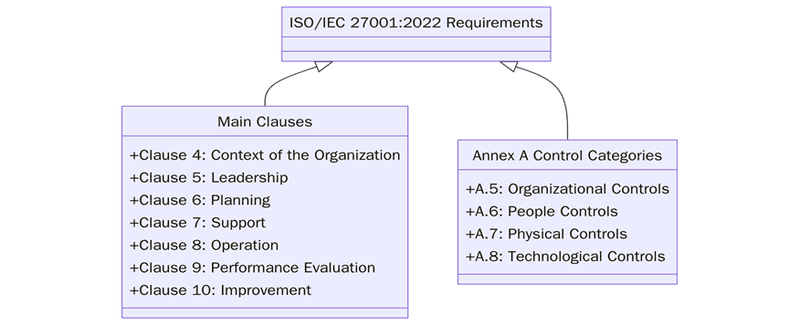
- Define the scope of the information security management system including locations processes information types and supporting assets.
- Establish an information security policy and measurable objectives linked to business needs.
- Identify interested parties and their needs such as customers staff regulators partners and suppliers.
- Conduct risk assessment and risk treatment for information assets with clear criteria and approved risk acceptance rules.
- Select and justify information security controls using the Annex A themes and any additional controls needed.
How to prepare for ISO/IEC 27001:2022 implementation?
Preparation for ISO/IEC 27001:2022 should focus on linking existing technical controls with a clear management system. Many companies already have firewalls backups and tools in place but they lack consistent risk records ownership and review. Below are some of the key preparation steps:
- Map your information assets including systems applications, data sets locations and key business processes.
- Identify where data is stored and processed in house cloud shared platforms and supplier environments.
- Perform a simple gap review against ISO/IEC 27001:2022 requirements to see which processes are missing or weak.
- Define scope in a way that covers the real security perimeter without becoming impossible to manage.
- Build or update risk assessment and risk treatment methods and run them on priority assets first.
- Align existing policies and procedures so they are consistent clear and usable by staff.
Certification audit
Stage 1 audit: Review of ISMS scope information assets context analysis risk assessment method policies objectives controls overview documented processes and readiness for Stage 2.
Stage 2 audit: Verification of implementation across selected systems locations and teams including evidence of risk treatment access control backup and recovery incident handling supplier control awareness and monitoring.
Nonconformities: Must be corrected with clear root cause analysis updated controls or documentation improved records and evidence that changes are in use.
Surveillance audits: Conducted annually to confirm that controls monitoring and reviews remain active as systems and threats change.
Recertification audits: Required every three years to review the full ISMS scope new technologies supplier changes and major business shifts.
What are the benefits of ISO/IEC 27001:2022?
ISO/IEC 27001:2022 helps organizations move from scattered security measures to a clear information security management system. It brings business leadership closer to technical work and gives customers a trusted reference point when they review vendors. Below are some of the key benefits:
- Clearer structure for managing information security risks instead of isolated technical fixes.
- Better alignment between IT security legal operations HR and business owners.
- Stronger control of access rights especially for high-risk systems and remote work setups.
- More reliable handling of incidents with defined reporting investigation and follow up.
- Improved supplier oversight where vendors host systems process data or provide support.
- Better evidence for customers partners and auditors during due diligence and vendor reviews.
Market trends
By 2026 more organizations will treat ISO/IEC 27001 as a base layer for all digital work. Cloud heavy environments and SaaS use will pull more suppliers into scope and audits will focus more on how you govern shared responsibility. Logs dashboards and automated alerts will be used as core evidence rather than static reports. At the same time pressure around privacy AI use and supply chain risk will push companies to link ISO/IEC 27001 with continuity, privacy, AI and resilience frameworks. Institutions that keep their ISMS aligned with real architecture and real risk will find audits more useful and easier to maintain.
Training and courses
Pacific Certifications provides accredited training programs. If your organization is looking for ISO/IEC 27001 training our team is equipped to help you.
· Lead Auditor Training: supports professionals who need to evaluate information security management systems across different industries.
· Lead Implementer Training: supports teams that are designing or upgrading an ISMS aligned with ISO/IEC 27001:2022.
How Pacific Certifications can help?
Pacific Certifications provides accredited audit and certification services for ISO/IEC 27001. We assess scope information assets risk assessment methods selected controls documented processes technical and physical safeguards supplier oversight internal audits and management reviews. We issue Certificates of Conformity following impartial audits and we do not provide consultancy or ISMS design services.
To request an ISO/IEC 27001:2022 audit plan or discuss information security certification scope for your organization contact [email protected] or visit www.pacificcert.com.
Ready to get ISO/IEC 27001 certified?
Contact Pacific Certifications to begin your certification journey today!
Author: Alina Ansari
Suggested Certifications –
Read more: Pacific Blogs

