ISO 27001:2022 Standard Explained for Data Protection and Compliance

Introduction
As the business activities are moving towards the cloud platforms, remote work, connected apps and third-party tools, data protection expectations are continuously increasing. During the vendor onboarding process, a lot of customers, asking what the ISO 27001 standard is and if a supplier can provide an information security management system which is verified by records, internal checks and with leadership oversights.
Organizations must comply not only with laws in their own country, but also with security clauses in contracts and industry rules that vary across regions, so, compliance pressure is also increasing. That is the reason why the searches like ISO 27001 compliance requirements, ISO 27001 data protection explained and ISO 27001 vs GDPR compliance are very closely linked to purchase intent. ISO 27001 makes it easier to turn compliance into effective controls like access control, risk assessment, incident response, supplier checks and secure handling of records.
This guide explains how ISO 27001 works, what ISO 27001 security controls mean in real operations and how to plan an ISO 27001 implementation guide that fits your scope. It also covers ISO 27001 certification requirements, ISO 27001 certification cost drivers and a realistic certification timeline. Get started with your certification process, contact us at [email protected] today! Data protection is not only a technical issue, it is a business trust issue.
Quick summary
ISO 27001 gives organizations a structured way to manage data protection, cybersecurity controls and compliance readiness through an information security management system. The most relevant standards are ISO/IEC 27001 (ISMS), ISO/IEC 27701 (privacy management) and ISO 22301 (business continuity), with additional options like ISO/IEC 27000 for ISMS terms and ISO 9001 for governance discipline. Certification strengthens trust with clients, regulators and partners while reducing data breach prevention risk through auditable controls.
Applicable ISO standards for data protection and compliance
ISO 27001 does not operate alone. Many organizations combine it with privacy and continuity standards to cover personal data handling, uptime needs and supplier risk.
Click here to find out more applicable standards to your industry: Pacific Certifications blogs
ISO/IEC 27001 for data protection and compliance (Information security management system)
ISO/IEC 27001 is the best-known standard for an information security management system. It helps you identify security risks, select controls, assign ownership and prove that controls are working through records and review routines. For data protection, ISO 27001 drives control of access rights, secure handling of data in systems, device controls, supplier checks, logging expectations and incident response steps. It also supports compliance mapping because you can link ISMS controls to legal and contractual requirements, including privacy rules and customer security clauses.
Read more: ISO/IEC 27001 certification
ISO/IEC 27701 for privacy compliance (Privacy management)
ISO/IEC 27701 is often selected when personal data handling is a primary risk. It helps formalize privacy management roles, data processing responsibilities, retention rules, data subject request handling and supplier controls for processors. This supports teams searching ISO 27001 GDPR compliance and ISO 27001 privacy management because it provides a structured privacy layer that can sit on top of the ISMS.
Read more: ISO/IEC 27701 certification
ISO 22301 for disruption readiness (Business continuity)
ISO 22301 supports continuity planning for disruptions that can affect data availability and service delivery. This includes ransomware events, cloud outages, vendor downtime and loss of key infrastructure. In practice, it supports business impact analysis, recovery priorities, tested response steps and alternate operating arrangements. When ISO 27001 security controls depend on backups, recovery testing and incident response, ISO 22301 helps make those plans measurable and repeatable.
Read more: ISO 22301 certification
ISO/IEC 27000 for ISMS clarity (ISMS overview)
ISO/IEC 27000 provides ISMS overview and common terms. It helps teams align on the ISO 27001 framework explained, especially when multiple departments are involved. This reduces confusion during implementation because scope, risk, assets, controls and evidence expectations are defined consistently.
What are the requirements for ISO 27001 certification?
Certification is not just about passing an external audit. It requires a working ISMS with documented rules and consistent evidence. Common ISO 27001 certification requirements include:
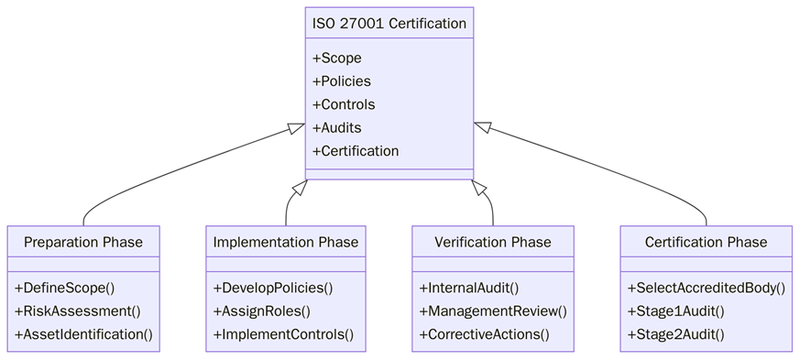
Defining scope: Define what the ISMS covers such as business units, locations, systems, cloud platforms and third-party services.
Information security policy and objectives: Maintain an ISO 27001 data protection policy with clear objectives and leadership ownership.
Risk assessment and treatment: Follow an ISO 27001 risk assessment guide to identify threats, assess impact and likelihood and define treatment plans.
Control selection and implementation: Implement ISO 27001 cybersecurity controls such as access control, secure configuration, logging, supplier controls and incident response.
Documented processes and evidence: Maintain procedures and records for access reviews, incident tickets, backup checks, training completion, supplier reviews and corrective actions.
Internal audits and management review: Run internal audits, fix nonconformities and complete leadership reviews that show decisions and follow ups.
Certification audit readiness: Prepare for a two-stage external audit with Stage 1 for documented readiness and Stage 2 for implementation verification.
Pro Tip:Start with a clear scope and a practical ISO 27001 implementation guide that focuses on access control, asset inventory, supplier risk checks, incident response and backup routines. If privacy is a primary driver, add ISO/IEC 27701 so ISO 27001 GDPR compliance mapping becomes easier and evidence stays consistent.
What are the benefits of ISO 27001 for data protection and compliance?
ISO certification brings significant benefits. These include:
Stronger client trust through an auditable information security management system
Clearer compliance mapping for security and privacy obligations, including ISO 27001 vs GDPR compliance discussions
Better data breach prevention ISO 27001 outcomes through risk based controls and incident readiness
Improved control of suppliers and third-party tools through structured review routines
Faster threat detection and response through logging discipline and incident response processes
Better governance through internal audits, corrective actions and management review routines
Stronger sales enablement because many buyers ask to get ISO 27001 certified before onboarding
Better alignment between technology teams and leadership because ownership and evidence are defined
Industry direction for the upcoming years supports why ISO 27001 remains a high demand certification. ISO describes ISO/IEC 27001 as the best known ISMS standard and outlines its role in establishing and improving an ISMS. In parallel, published market forecasts project cybersecurity spending growth through 2030, including projections that the cybersecurity market could reach hundreds of billions of USD by 2030. (source: MarketsandMarkets) For privacy context and regulatory alignment, the GDPR legal text is available on the official EU legal portal and is commonly used for control mapping when teams discuss ISO 27001 vs GDPR compliance. (source: EUR-Lex)
ISO 27001 certification cost for data protection and compliance
ISO 27001 certification cost depends on ISMS scope, number of locations, employee count, system complexity and supplier footprint. Cost also changes based on how much evidence already exists for access control reviews, asset inventories, incident handling, backup checks and internal audits. Organizations looking for affordable ISO 27001 certification often reduce scope creep by defining clear boundaries and focusing on high-risk systems first. Ongoing costs also include surveillance audits during the certification cycle.
Contact [email protected] for a free ISO 27001 certification cost quote aligned to your data protection and compliance needs.
ISO 27001 certification timeline
The certification timeline depends on readiness and scope size. Many organizations complete implementation in phases, starting with risk assessment, control rollout, evidence collection and internal audits. The external audit typically runs in two stages, with Stage 1 focused on documented system review and Stage 2 focused on implementation verification through records and interviews. Teams with disciplined access management, ticket-based incident handling and clear supplier management records usually move faster.
How Pacific Certifications can help?
Pacific Certifications, accredited by ABIS, audits and certifies organizations seeking ISO 27001 for data protection and compliance. Whether you operate in IT services, SaaS, finance, healthcare, manufacturing, or professional services, we provide independent third-party certification audits aligned to the ISO 27001 framework.
Here’s why organizations choose us for ISO 27001 certification needs:
Our auditors focus on practical evidence aligned to ISO 27001 security controls and ISMS scope
We provide clear audit plans and transparent audit reports aligned to ISO 27001 certification requirements
We support integrated audits when ISO/IEC 27701 or ISO 22301 is included in scope
We plan audits to reduce disruption and support remote evidence review where applicable
We support certification cycle needs including surveillance audits and recertification audits
Contact Us
If you need more support with ISO 27001 Certification, contact us at [email protected] or +91-8595603096.
Author: Alina Ansari
Read More At: Blogs by Pacific Certifications

